
Tencent looks forward to working with the security community to find vulnerabilities in order to keep our businesses and customers safe. If you believe you have discovered a vulnerability, kindly disclose to us responsibly via the Tencent Security Response Centre (TSRC). This Bounty Policy governs your participation in the bounty program and it forms part of, and is subject to, the Tencent Security Response Center Terms of Service.
Please note that due to the involvement of a third-party payment provider, overseas payments are subject to a longer processing time. If there are any questions, please feel free to contact our TSRC team by leaving a message on your vulnerability report.
Rules of Engagement
The classification of a vulnerability (Critical, High, Moderate or Low as described below), whether a product or application is in scope of the bounty program and its classification (core, important, and other in-scope), and whether to grant a monetary reward and its amount will be within the sole discretion of the Tencent Security Team, based on a number of factors including, without limitation, quality of the report, severity of the vulnerability, reproducibility of the vulnerability, its impact on our users and other products and services, ease of exploitation and many other factors.
Any design or implementation issue regarding any qualifying product that is reproducible and substantially affects the security of Tencent users is likely to be in scope for the program.
However, reports and researchers must meet the following requirements to be eligible to receive a monetary reward:
- You must be above the age of 13. If you are between the ages of 13 and 18 (or the relevant age in your jurisdiction where you are considered a minor), your parent or guardian must agree to the Agreement (both for themselves and on your behalf) before you can submit reports.
- You must be the first reporter of the vulnerability (whether you are the first reporter is determined by us in our discretion and we are not obligated to share with you details related to prior reports).
- Your report must be your own work, and you have not used information owned by another person or entity.
- Please provide detailed reports with reproducible steps. If the report is not detailed enough to reproduce the issue, the issue will not be eligible for a reward.
- Submit one vulnerability per report, unless you need to chain vulnerabilities to provide impact.
- Multiple vulnerabilities caused by one underlying issue will be awarded one bounty.
- The vulnerability must demonstrate security impact to a site or application in scope (see Scope below)
- Accessing private information of other users, performing actions that may negatively affect Tencent users (e.g., spam, denial of service), or sending reports from automated tools without verifying them will immediately disqualify the report, and may result in additional steps being taken. You must comply with applicable laws and regulations, including applicable privacy laws, with respect to your disclosure and access of data.
- When testing, you must only use and only interact with your own test accounts in order to respect our users’ privacy, especially those which may compromise the privacy of others. You will not interact with another user’s account without that user’s prior written consent (which you will make available to us upon our request).
- Vulnerability Disclosure:
- It is strictly forbidden to publicly disclose the vulnerability prior to the report being closed by us, the vulnerability being fixed and you receiving a written authorization from us.
- The disclosure and the content of the disclosure should be under the authorization of TSRC. Please take note that any form of vulnerability disclosure prior to consent from Tencent may result in disqualification from the Bounty program.
- Feel free to contact us if you have any questions.
- We are prohibited from rewarding you (such as when you are subject to trade sanctions, embargoes or denied person status).We are unable to issue rewards to individuals employed by Tencent or its subsidiaries.
Grant of License
You grant Tencent a non-exclusive, royalty-free, irrevocable, perpetual, transferable, worldwide license (with the right to sublicense) to copy, reproduce, use, modify, test, create derivative works (including commercial products) based upon, distribute, publish, display and otherwise exploit your reports and other information you provide to us under this Agreement.
Rewards
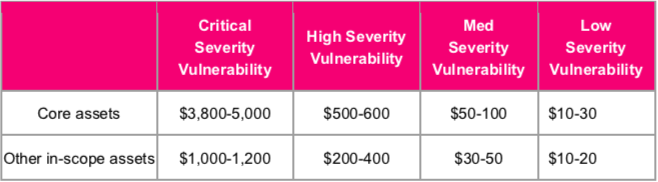
Rewards are stated in USD.
Severity Rating
[Critical]

[High]

[Moderate]
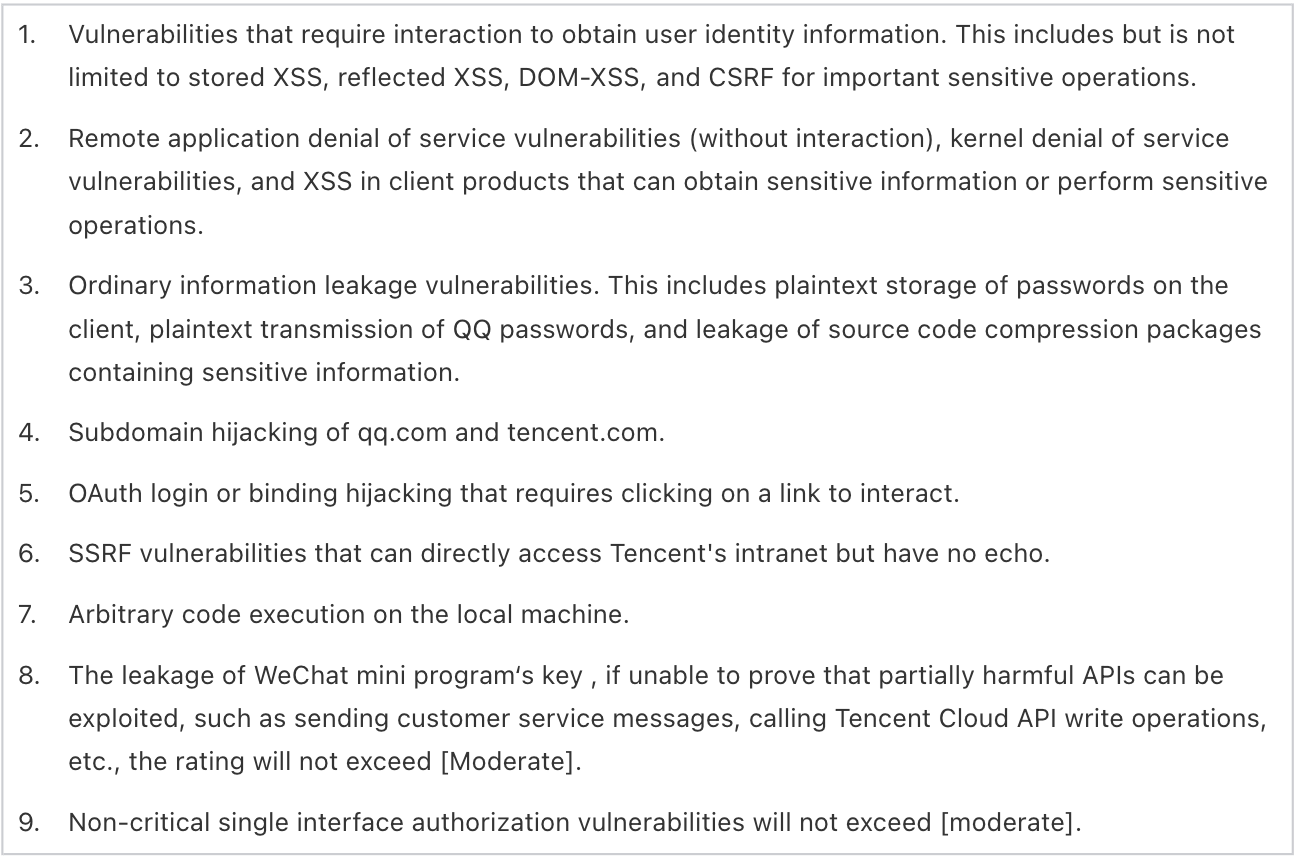
[Low]

All reports will be reviewed based on the impact and severity of the reported vulnerability. Any qualifying report that results in a change being made will at a minimum receive the Hall of Fame recognition.
The main categories of vulnerabilities that we are primarily concerned about are:
- Cross-site Scripting (XSS)
- Cross-site Request Forgery (CSRF)
- Server-Side Request Forgery (SSRF)
- SQL Injection
- Remote Code Execution (RCE)
- XML External Entity Attacks (XXE)
- Access Control Issues (Insecure Direct Object Reference issues, etc.)
- Exposed Administrative Panels that without strong protection
- Directory Traversal Issues
- Local File Disclosure (LFD)
- Vast Users’ Sensitive Information Leakage
- Vast Order details Leakage
In-Scope Assets
Products, services and applications distributed and made available in any form by or on behalf of Tencent and described in “Core Products” and “Other In-Scope Products” below are in scope. For more information about our products and services, please visit https://www.tencent.com/en-us/business.html.
1. Core Assets
Tencent Yuanbao (Android, iOS, Web)
Tencent Yuanqi (Android, iOS, WinPC, Mac)
WeChat (Android, iOS, WinPC, Mac)
WeChat instant messaging function
WeChat login/ticket
WeChat address book
WeChat Moments
WeChat Official Account
WeChat Mini Program main framework API
WeCom (Android, iOS, WinPC, Mac)
Tencent Exmail main domain (*.exmail.qq.com)
WeCom management background
WeCom address book
WeCom instant messaging function
QQ mail main domain (*.mail.qq.com)
WeCom basic core functions (WeCom instant messaging function, enterprise payment, session content archive, Weiyun, document, fusion meeting, WeCom Moments)
WeCom Sensitive information, such as enterprise address book list, login/ticket
WeChat Pay function (excluding services recommended on the payment guide page grid)
WeChat wallet
WeChat Pay independently-developed face recognition device
WeChat Pay independently-developed palm recognition device
WeChat Pay merchant platform (including domestic and overseas)
WeChat Credit card repayment
Tenpay
LiCaiTong
Tencent mobile top-up
Tencent Portfolio (腾讯自选股)
King of Glory mobile game
Game for Peace mobile game
Tencent Games Joy Club
jiazhang.qq.com (成长守护平台)
QQ client (Android, iOS, WinPC, Mac)
QQ basic core functions (such as instant messaging function, user profile, login/ticket, etc.)
QQ wallet (excluding services recommended on the wallet guide page grid)
Doc.qq.com (excluding third-party provided plugins)
Tencent Video main website and mobile APP (Android, iOS)
Voov Meeting
Tencent Cloud (computing/container and middleware/storage/network and CDN/security) (Refer to corresponding products in Tencent Cloud Product Overview - Tencent Cloud https://cloud.tencent.com/product)
Tencent PC Manager / Tencent Mobile Manager
2. Other In-Scope Assets:
It includes the majority of Tencent's products and businesses, such as Tencent Game Helper (腾讯游戏助手), Tencent Ride Code Mini Program(腾讯乘车码小程序), QQ Music and other products, including but not limited to mobile applications, clients, mini programs, web sites, hardware, IoT, server services, and other product models.
3. *Notes about Tencent Cloud (cloud.tencent.com as included in *.tencent.com)
Only vulnerabilities affecting the platform itself and IP owned by Tencent will be accepted. If an IP belongs to Tencent Cloud external customer, it is not considered in scope.
Test Plan
You can use a QQ or Wechat account to log into all Tencent’s products and services.
1. To register a QQ account, please go to https://ssl.zc.qq.com/v3/index-en.html?type=0 and follow the instructions.
2. To register a WeChat account, please download an WeChat app from App store or through Android system, then follow the registration guide.
Once you have a QQ or WeChat account, you can start testing.
Out-of-Scope Vulnerabilities
When reporting vulnerabilities, please consider (1) attack scenario / exploitability, and (2) security impact of the bug. The following issues are considered out of scope (either ineligible or false positives):
- "Self" XSS
- Session fixation
- Content Spoofing
- Missing cookie flags
- SSL/TLS best practices
- Mixed content warnings
- Clickjacking/UI redressing
- Flash-based vulnerabilities
- Admin panel can be brute force
- Local denial of service of Mobile APP
- Reflected file download attacks (RFD)
- Physical or social engineering attacks
- Feedback,comment,message,etc. flooding
- SMS/Email flooding for some of our business
- CSRF/XSS with long or unpredictable parameter
- Login/logout/unauthenticated/low-impact CSRF
- Unverified Results of automated tools or scanners
- No SPF/DMARC in non-email domains/subdomains
- Attacks requiring MITM or physical access to a user's device
- Issues related to networking protocols or industry standards
- Error information disclosure that cannot be used to make a direct attack
- Missing security-related HTTP headers which do not lead directly to a vulnerability
- Information leakage that cannot be used to make a direct attack,like server IP,server version,path,error message,internal IP,etc.
Detecting SSRF
We have set up a "demo" service for SSRF testing. If you believe you have an SSRF in production, please use either of the following IP/port combinations for testing:
http://9.138.237.216/flag.html aka http://tst.woa.com/flag.html
This service will accept HTTP requests to any endpoint, of any request type, and will return a secret token in both headers and response body.





